Hi Folks,
Given my profession and my love of gadgets and control, securing our ever more connected tanks is something very close to my heart.
We are increasingly using monitors such as SenEye, tank controllers (including Apex and GHL) and other connected equipment to run critical aspects of our marine tanks. From controlling flow, regulating temperature, dosing additives and even performing water changes and controlling salinity.
Recently however, many people have been wanting more access to their systems whilst away from their tanks and have started to expose these devices to the internet. Many using port forwarding on their router, which allows remote access to any device configured to use it.
This often means that ANYONE can find and potentially connect to the device also. Worse still, what if it still had the default username and password!?
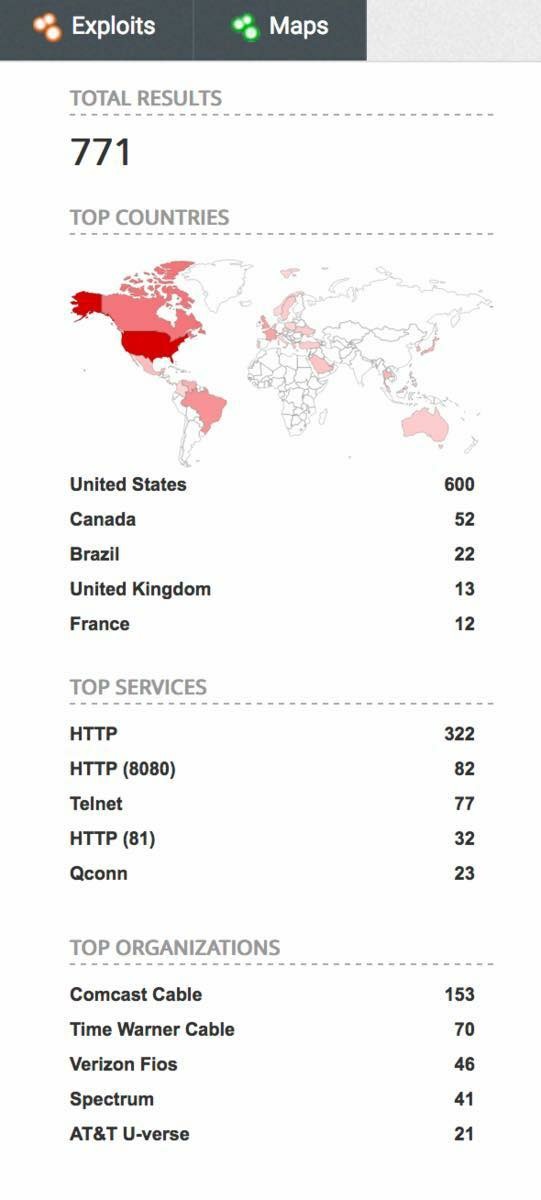
The graphic above shows the distribution and number of aquarium controllers exposed to the internet in this quick search.
We need to think about security!
Imagine the damage that could be caused if someone had access to your tank controller or connected device. What would happen if the tank temperature plummeted, or rose, pumps stopped, RO dumped or alk solution over dosed? The consequences could be catastrophic.
In addition, by exposing many of these devices to the internet, you could be providing a hacker with an opportunity to hack into any network it is connected to and give access to other systems and devices connected to your home network. Such attacks are frequent and relatively easy, as these devices are NEVER intended to be exposed to the internet.
So, I wanted to share with you just a little of my findings, whilst searching for just one particular type of popular aquarium controller.
- 771 users of one type of aquarium controller have their admin pages exposed to the internet & are publicly available
- Many appear to be using the default username and password, published in the user manual
- At least One is owned by an aquarium maintenance company and exposes their client’s network
Last month, one of the keynotes at the largest cyber security conference, called RSA, was about a cyber attack launched on a Casino. The attackers gained access via an aquarium controller that had been exposed to the internet.
https://www.washingtonpost.com/news...-casino/?noredirect=on&utm_term=.4d76eaf0e3f0
So now EVERYONE is looking for these devices.
What can you do to help make sure your tank is secure?
1: ALWAYS use the cloud service (Fusion, MyGHL etc) rather than local interface when away from the tank, if at all possible.
2: NEVER expose the admin address of any such device to the internet, either directly or by using port forwarding
3: ALWAYS change the default username and password (to a different username than "Admin" and a strong password)
4: Connect SECURELY to your home network using a VPN or remote control app if you need access to the local admin address
You have been warned...
PS: The vendor of the controllers shown above has been contacted with full details, so that they can help their customers stay secure. This isn't a security flaw with any controller in particular.
Given my profession and my love of gadgets and control, securing our ever more connected tanks is something very close to my heart.
We are increasingly using monitors such as SenEye, tank controllers (including Apex and GHL) and other connected equipment to run critical aspects of our marine tanks. From controlling flow, regulating temperature, dosing additives and even performing water changes and controlling salinity.
Recently however, many people have been wanting more access to their systems whilst away from their tanks and have started to expose these devices to the internet. Many using port forwarding on their router, which allows remote access to any device configured to use it.
This often means that ANYONE can find and potentially connect to the device also. Worse still, what if it still had the default username and password!?
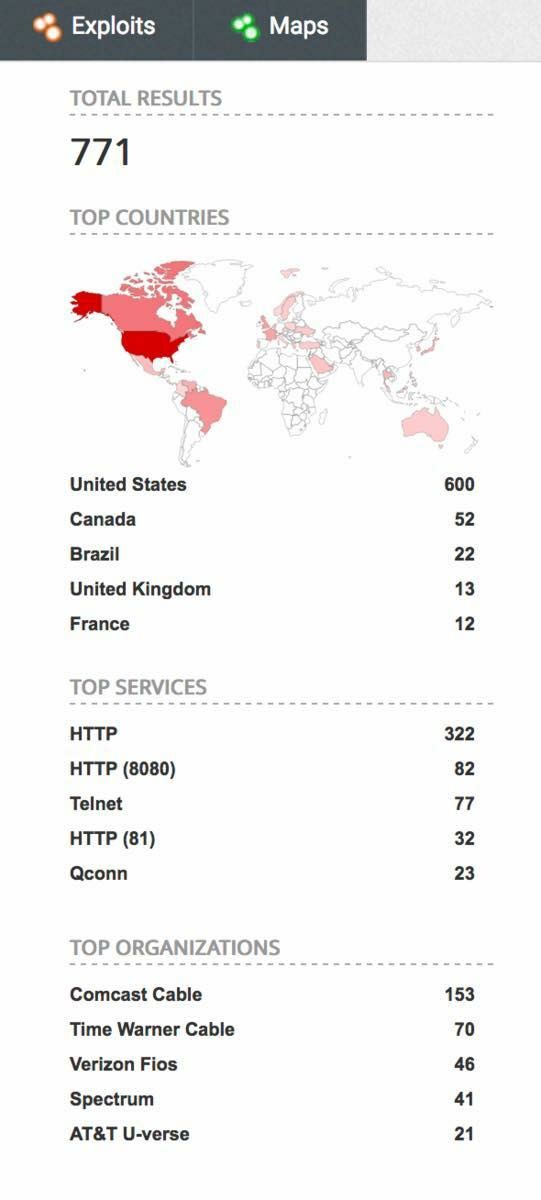
The graphic above shows the distribution and number of aquarium controllers exposed to the internet in this quick search.
We need to think about security!
Imagine the damage that could be caused if someone had access to your tank controller or connected device. What would happen if the tank temperature plummeted, or rose, pumps stopped, RO dumped or alk solution over dosed? The consequences could be catastrophic.
In addition, by exposing many of these devices to the internet, you could be providing a hacker with an opportunity to hack into any network it is connected to and give access to other systems and devices connected to your home network. Such attacks are frequent and relatively easy, as these devices are NEVER intended to be exposed to the internet.
So, I wanted to share with you just a little of my findings, whilst searching for just one particular type of popular aquarium controller.
- 771 users of one type of aquarium controller have their admin pages exposed to the internet & are publicly available
- Many appear to be using the default username and password, published in the user manual
- At least One is owned by an aquarium maintenance company and exposes their client’s network
Last month, one of the keynotes at the largest cyber security conference, called RSA, was about a cyber attack launched on a Casino. The attackers gained access via an aquarium controller that had been exposed to the internet.
https://www.washingtonpost.com/news...-casino/?noredirect=on&utm_term=.4d76eaf0e3f0
So now EVERYONE is looking for these devices.
What can you do to help make sure your tank is secure?
1: ALWAYS use the cloud service (Fusion, MyGHL etc) rather than local interface when away from the tank, if at all possible.
2: NEVER expose the admin address of any such device to the internet, either directly or by using port forwarding
3: ALWAYS change the default username and password (to a different username than "Admin" and a strong password)
4: Connect SECURELY to your home network using a VPN or remote control app if you need access to the local admin address
You have been warned...
PS: The vendor of the controllers shown above has been contacted with full details, so that they can help their customers stay secure. This isn't a security flaw with any controller in particular.















