In my pursuit to trigger feed and maintenance modes using a single push button, I have come across a few challenges. Sure I have a Profilux 4 controller which handles most of my pumps and such. And my plans include connecting some buttons to trigger the modes (likely something from Harry's Aquatics as shown here). However my VorTech MP40 pump which is controlled by the Mobius app or its own controller doesn't (yet) play well with others.
Ok so that is a simple enough hypothesis and the solution will be a bit more complicated. But here was my thought process.
If (a) the BLE (Bluetooth Low Energy) messages being sent to the VorTech pump from the Mobius app can be captured, and (b) a DIY device controlled with a 0-10V interface can send BLE messages, then (c) the VorTech pump can be controlled with a 0-10V interface.
(a) + (b) = (c) Right?
Once the btsnoop_hci.log is produced it can be opened with Wireshark on a computer. Without any filtering Wireshark will show all of the captured messages. This could be hundreds if not thousands of messages. So finding out which messages are meant for the VorTech controller is crucial. Luckily there is an app for that.
The nRF Connect app is great for discovering and testing different BLE devices. Scanning with the app will find all nearby devices. When I filtered for a "mobius" device it resulted in the following:
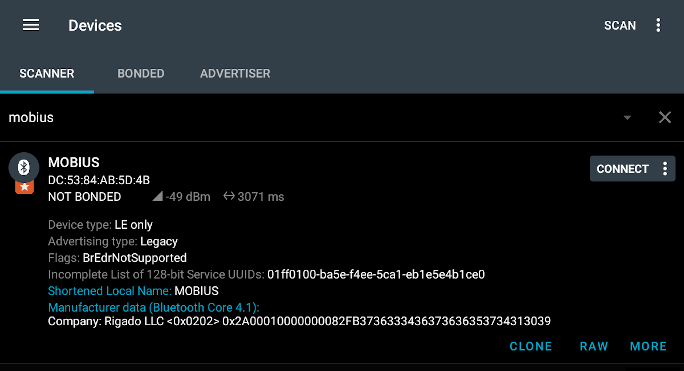
This shows that my Mobius device has an address of DC:53:84:AB:5D:4B. This piece of information will help drastically reduce the number of relevant messages in the log. Back in Wireshark a filter can be created to only show Bluetooth messages addressing the Mobius device so both sent and received messages are viewable.
The last thing I did before turning off Bluetooth (thus stopped collecting messages) was to start a scene for ~20 seconds and then stop it. This allowed me to scroll to the bottom of the filtered logs and start working backwards to see what was actually sent. And sure enough, there were two messages sent from my device to the Mobius device ~20 seconds apart.
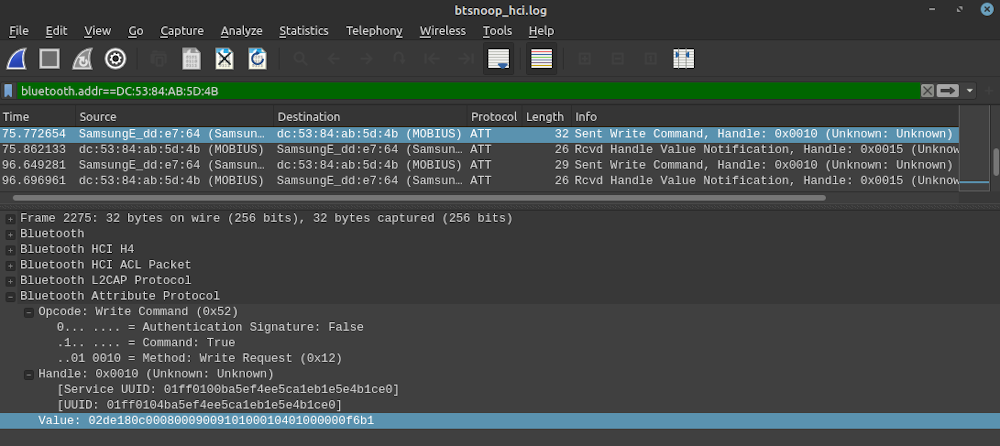
And there it is. The value (in my case 02de180c0008000900910100010401000000f6b1) which appears to start the feed scene. It also shows which BLE service UUID and characteristic UUID the message it was sent to. The nRF Connect app now can be used to test the BLE message. Once connected to the Mobius device through the nRF Connect app, a list of available unknown services will be displayed. Once the corresponding characteristic is found using the UUIDs, the app can also attempt to send messages to the characteristic.
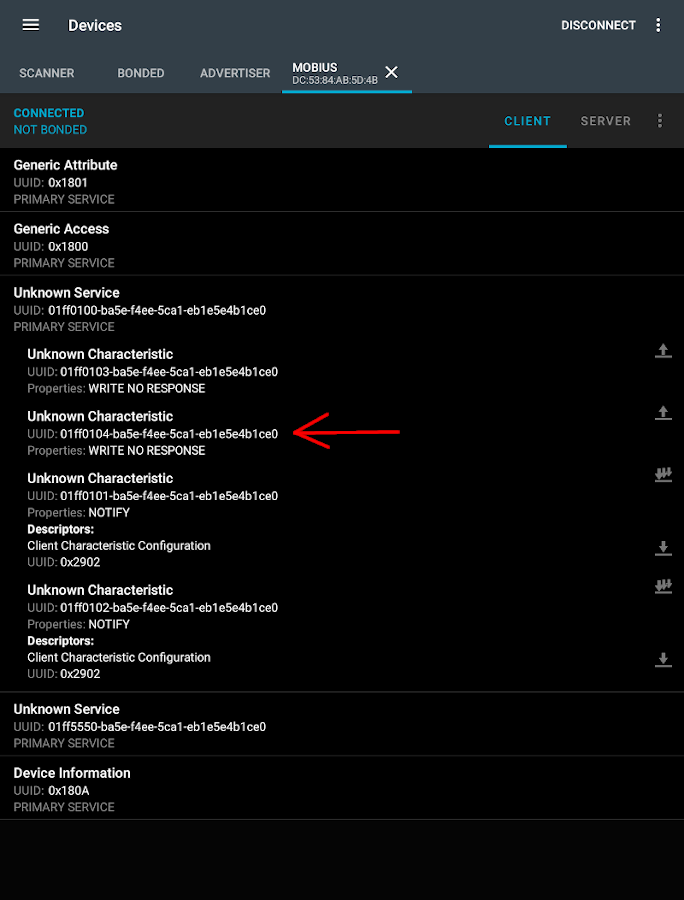
Ta-da! When the same value is sent to the same characteristic using the nRF Connect app the VorTech pump starts the feed scene. The same is true for stopping the scene (which was the value sent ~20 seconds after the start value in the logs). This is enough to prove the BLE messages sent to VorTech pumps can be spoofed/mimicked/replicated.
More investigation will show the value being sent by the Mobius app changes slightly every time even though the scene doesn't change. Of course this piqued my curiosity and I started to deduce their meanings. So far I've identified a few parts for a couple difference messages. But I will provide what I have found in a separate following post.
There are many helpful write-ups about this sort of effort online. Just search for something like "reverse engineering bluetooth" and read through a couple.
The ADC is needed to take 0-10V input signals and give them a digital value. However, similar to many other microcontrollers, the Arduino Nano 33 BLE can't handle a full 10V signal. So a simple voltage divider needs to be added to drop the input signal down to 0-3V before it gets to the analog pin.
With the voltage divider in place some simple code for the Arduino will allow the board to do different things for different input signals. For my proof of concept I chose to do nothing until the input signal was equivalent to 4V or higher (simple math allows the digital value to represent 0-10V so the programming logic can match the original signal value).
The ArduinoBLE library can be used to find & connect a device, find the characteristic on the device, and write a value to that characteristic. So using the values captured during part (a) of this effort, a simple Arduino program can be written to do just that for the VorTech pump when triggered by the input signal.
Success! ;Woot
As a proof of concept this worked for a single Mobius scene with a single pump. However, I believe it would also work for multiple Mobius scenes and is not limited to just pumps. That's right. This technique should also work for any of the Mobius enabled devices which use BLE to communicate to the Mobius app.
Hypothesis:
A Mobius controlled VorTech pump can be controlled using a 0-10V interface.Ok so that is a simple enough hypothesis and the solution will be a bit more complicated. But here was my thought process.
If (a) the BLE (Bluetooth Low Energy) messages being sent to the VorTech pump from the Mobius app can be captured, and (b) a DIY device controlled with a 0-10V interface can send BLE messages, then (c) the VorTech pump can be controlled with a 0-10V interface.
(a) + (b) = (c) Right?
(a) Capturing BLE Messages
Sniffing Bluetooth traffic can be done in a couple different ways. The easiest and most convenient way is having the device (phone or tablet) which sends the messages to also log the traffic. Android devices have such a feature. Enabling Developer mode on an Android device provides the "Bluetooth HCI snoop log" option. Once the logging option is enabled simply use the Mobius app to turn on/off different "Scenes". I started very simple and noted when a scene was started and stopped.Once the btsnoop_hci.log is produced it can be opened with Wireshark on a computer. Without any filtering Wireshark will show all of the captured messages. This could be hundreds if not thousands of messages. So finding out which messages are meant for the VorTech controller is crucial. Luckily there is an app for that.
The nRF Connect app is great for discovering and testing different BLE devices. Scanning with the app will find all nearby devices. When I filtered for a "mobius" device it resulted in the following:
This shows that my Mobius device has an address of DC:53:84:AB:5D:4B. This piece of information will help drastically reduce the number of relevant messages in the log. Back in Wireshark a filter can be created to only show Bluetooth messages addressing the Mobius device so both sent and received messages are viewable.
The last thing I did before turning off Bluetooth (thus stopped collecting messages) was to start a scene for ~20 seconds and then stop it. This allowed me to scroll to the bottom of the filtered logs and start working backwards to see what was actually sent. And sure enough, there were two messages sent from my device to the Mobius device ~20 seconds apart.
And there it is. The value (in my case 02de180c0008000900910100010401000000f6b1) which appears to start the feed scene. It also shows which BLE service UUID and characteristic UUID the message it was sent to. The nRF Connect app now can be used to test the BLE message. Once connected to the Mobius device through the nRF Connect app, a list of available unknown services will be displayed. Once the corresponding characteristic is found using the UUIDs, the app can also attempt to send messages to the characteristic.
Ta-da! When the same value is sent to the same characteristic using the nRF Connect app the VorTech pump starts the feed scene. The same is true for stopping the scene (which was the value sent ~20 seconds after the start value in the logs). This is enough to prove the BLE messages sent to VorTech pumps can be spoofed/mimicked/replicated.
More investigation will show the value being sent by the Mobius app changes slightly every time even though the scene doesn't change. Of course this piqued my curiosity and I started to deduce their meanings. So far I've identified a few parts for a couple difference messages. But I will provide what I have found in a separate following post.
There are many helpful write-ups about this sort of effort online. Just search for something like "reverse engineering bluetooth" and read through a couple.
(b) Send BLE Messages Based on 0-10V Input
There are a few available options which are capable of sending BLE messages and able to read analog signals. While a Raspberry Pi device was my second choice, I decided to use an Arduino Nano 33 BLE because they have an ADC (Analog to Digital Converter) built-in. They can also be powered by a button/coin battery which is something I eventually want.The ADC is needed to take 0-10V input signals and give them a digital value. However, similar to many other microcontrollers, the Arduino Nano 33 BLE can't handle a full 10V signal. So a simple voltage divider needs to be added to drop the input signal down to 0-3V before it gets to the analog pin.
With the voltage divider in place some simple code for the Arduino will allow the board to do different things for different input signals. For my proof of concept I chose to do nothing until the input signal was equivalent to 4V or higher (simple math allows the digital value to represent 0-10V so the programming logic can match the original signal value).
The ArduinoBLE library can be used to find & connect a device, find the characteristic on the device, and write a value to that characteristic. So using the values captured during part (a) of this effort, a simple Arduino program can be written to do just that for the VorTech pump when triggered by the input signal.
(c) Controlling a VorTech Pump
After a few trial and error attempts (with some additional Arduino debugging/logging), I was indeed able to activate a feed scene on my VorTech pump when I supplied over 4V as input to the Arduino board. Now the VorTech pump can still be managed by the Mobius app AND the feed scene can be triggered by my Profilux 4 controller.Success! ;Woot
As a proof of concept this worked for a single Mobius scene with a single pump. However, I believe it would also work for multiple Mobius scenes and is not limited to just pumps. That's right. This technique should also work for any of the Mobius enabled devices which use BLE to communicate to the Mobius app.